
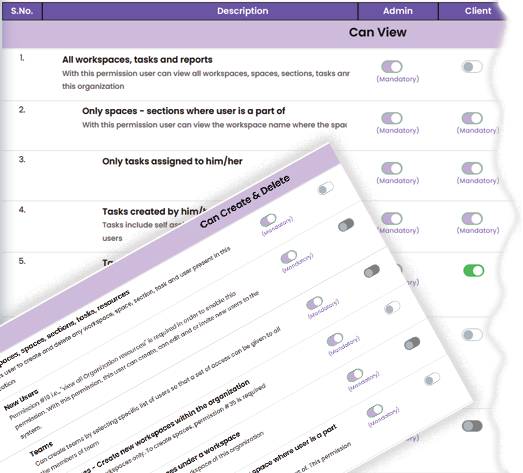
With Role-Based Access Control (RBAC), set customize access permissions, granting individuals only the necessary privileges to perform their roles effectively. This targeted approach fortifies your data against unauthorized access and ensures confidentiality, integrity, and availability
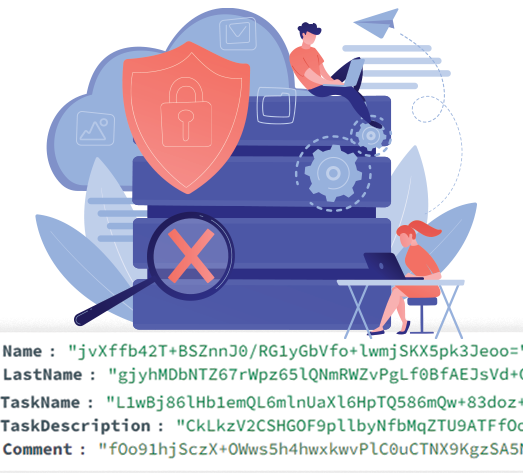
Our comprehensive encryption strategy extends to all sensitive fields, including user names, email addresses, task names, task descriptions, and comments. This ensures that your valuable information remains safeguarded against unauthorized access at all times. With every pertinent field encrypted, you can trust in the robust security measures implemented to protect your data and maintain confidentiality.


With Role-Based Access Control (RBAC), set customize access permissions, granting individuals only the necessary privileges to perform their roles effectively. This targeted approach fortifies your data against unauthorized access and ensures confidentiality, integrity, and availability

Our comprehensive encryption
strategy extends to all sensitive fields, including user names, email addresses,
task names, task descriptions, and comments. This ensures that your valuable
information remains safeguarded against unauthorized access at all
times.
With every pertinent field
encrypted, you can trust in the robust security measures implemented
to protect your data and maintain confidentiality.